I believe effective information protection is all about letting people make simpler choices around security – and preferably making as many of the important choices for them depending on the context in which they are working.
In short, proper information protection should generally “just work” as much as possible and let us focus our brain power on what most important for us.
Organizations are already commonly classifying documents and some have also opted to extend sensitivity labeling to other contexts like Teams teams, SharePoint sites, Power BI and Azure.
Bringing all of this together requires some kind of automation. A good place to start building that automation is through classifying workspaces and letting that sensitivity determination inherit to work done in those workspaces – but more on that in a bit.
Importantly, a brand new scenario has now opened up – Sensitivity Labeling for Teams meetings. Let’s take a look at how this works from a user’s perspective.
What do you mean you never look at meeting options?
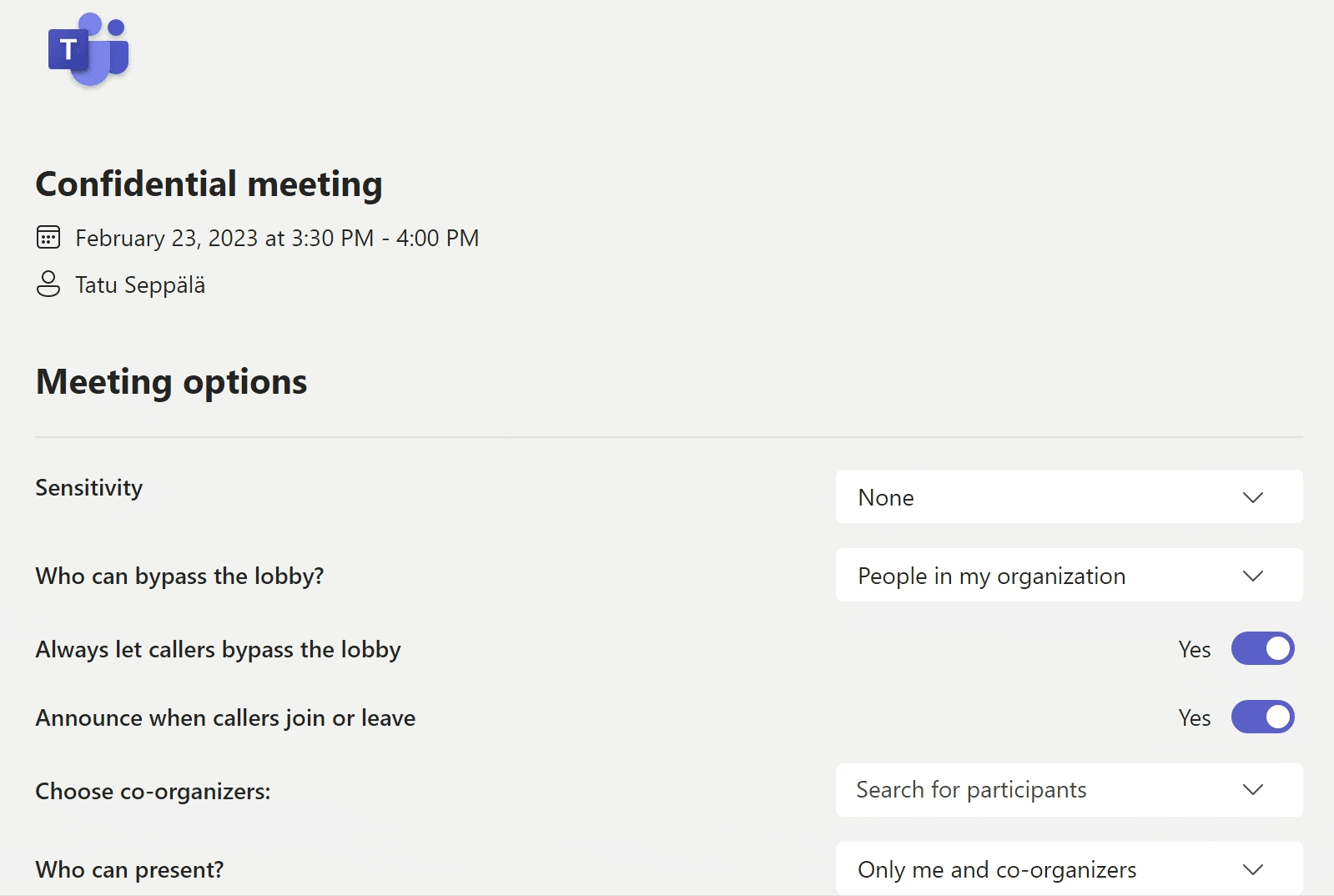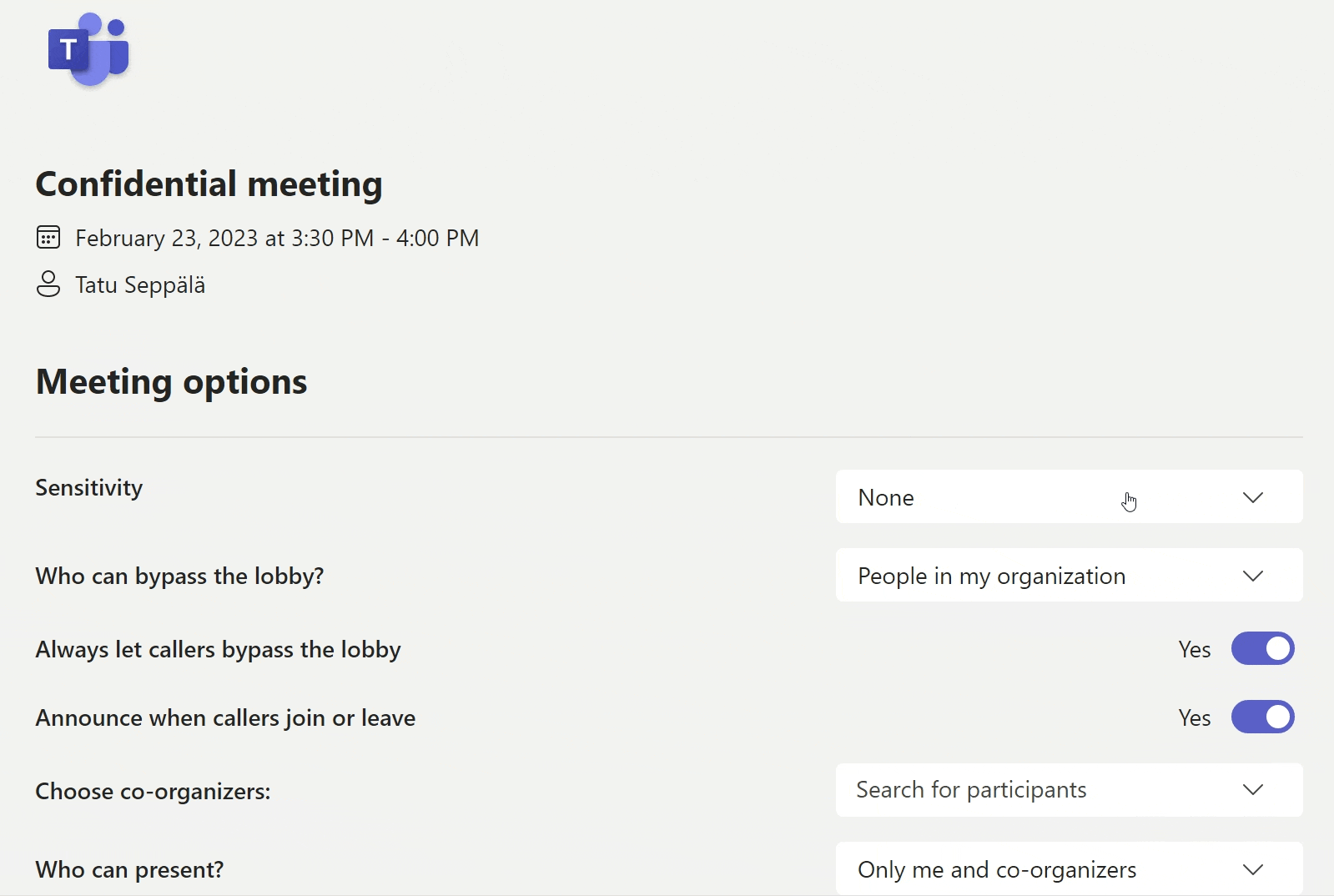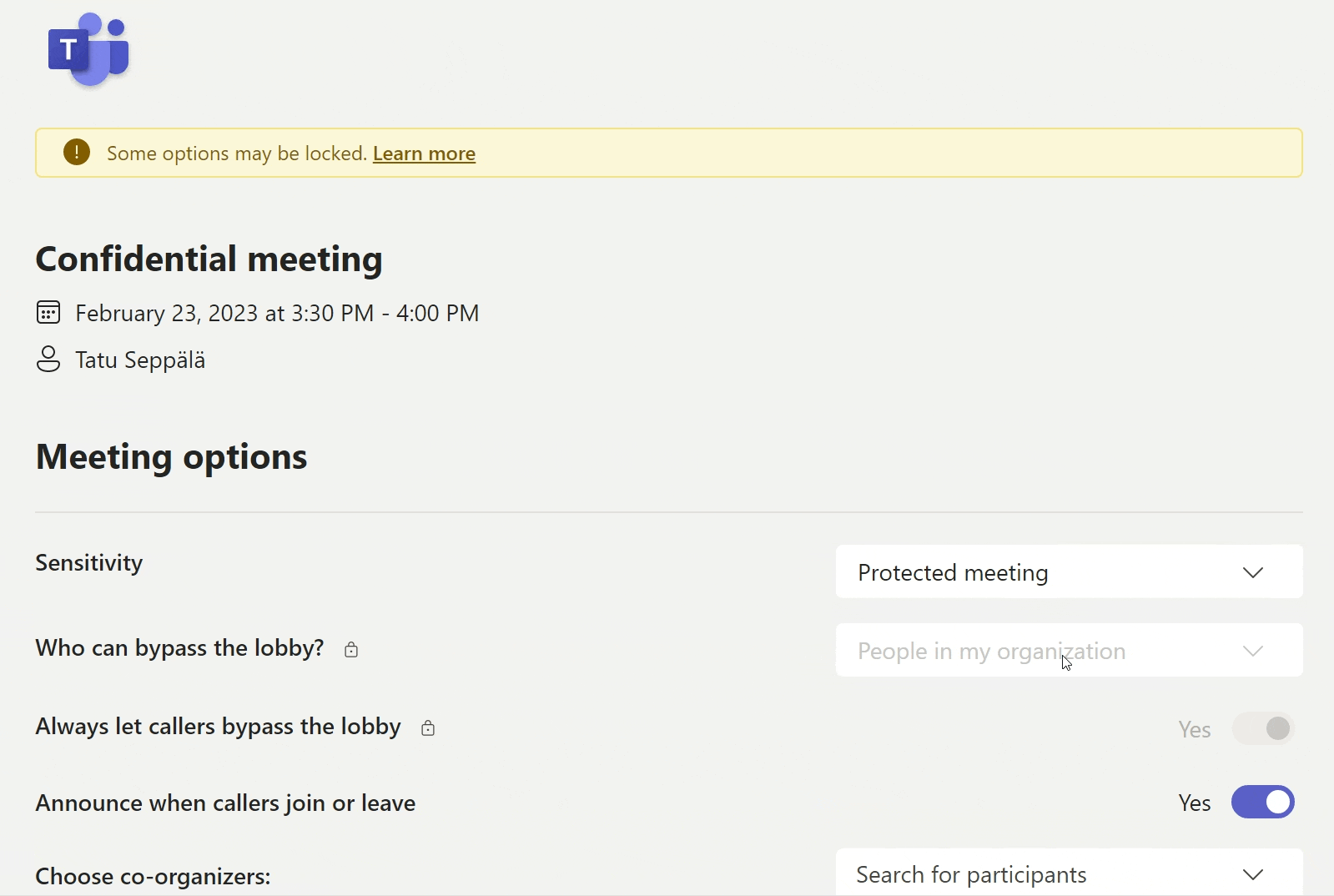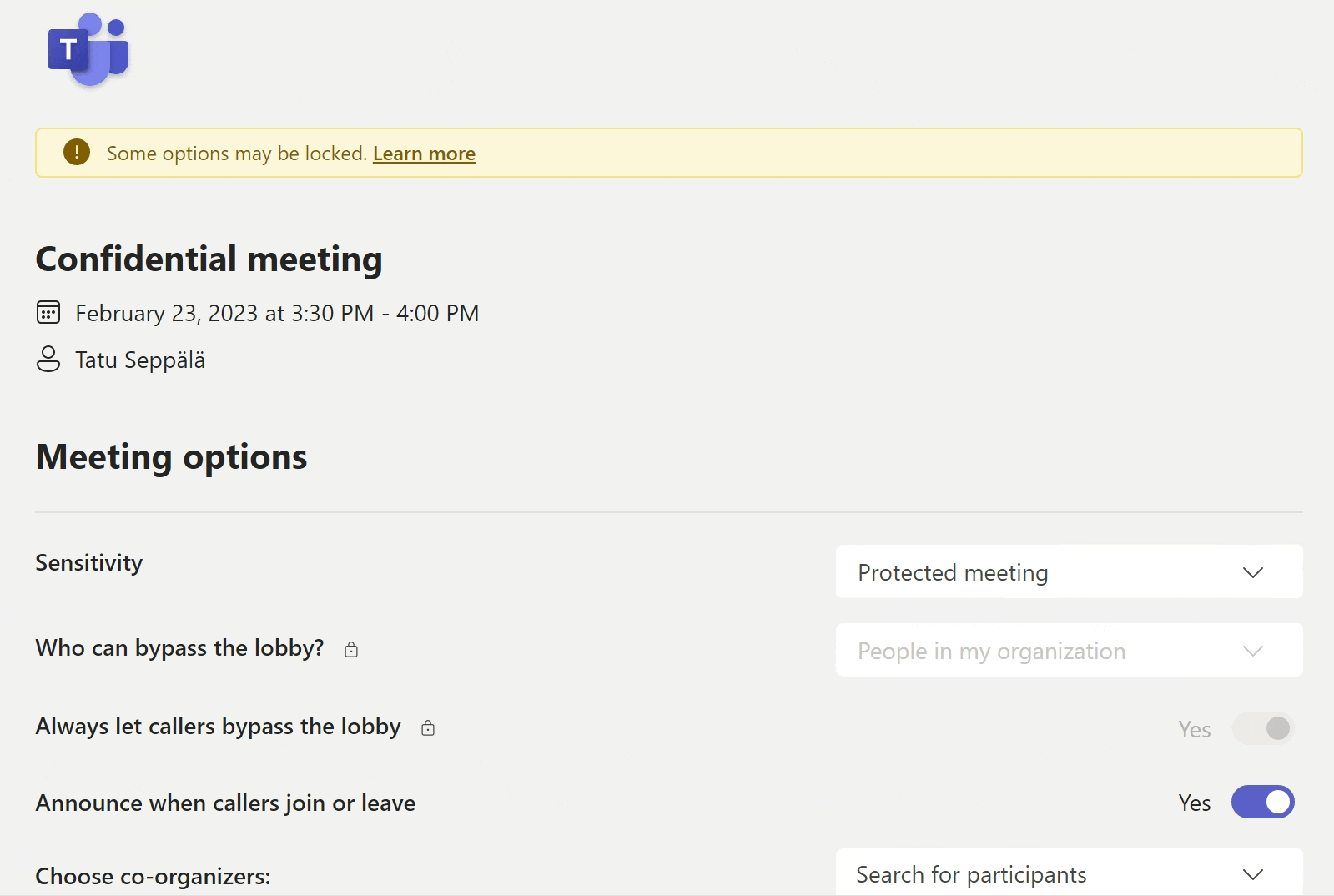
When creating a new Teams meeting, you might have seen the Meeting Options button.
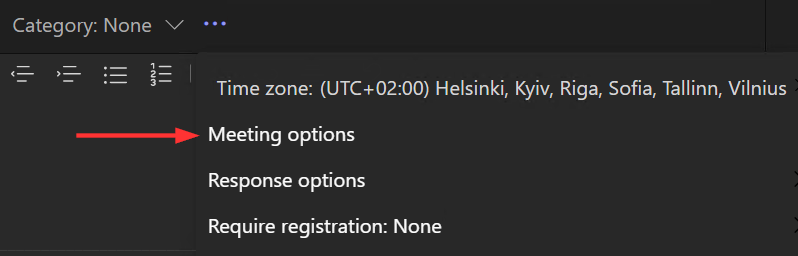
If you think back to the last 10 meetings you booked, for how many of those did you visit the options to fine-tune things?
Not too many? Yeah, me neither. That’s a shame because many of the controls for making Teams Meetings more purposeful and secure are hidden away there.
Below is a quick look at the many aspects of a meeting we can influence. See if you can spot the ones with direct security and risk management implications.
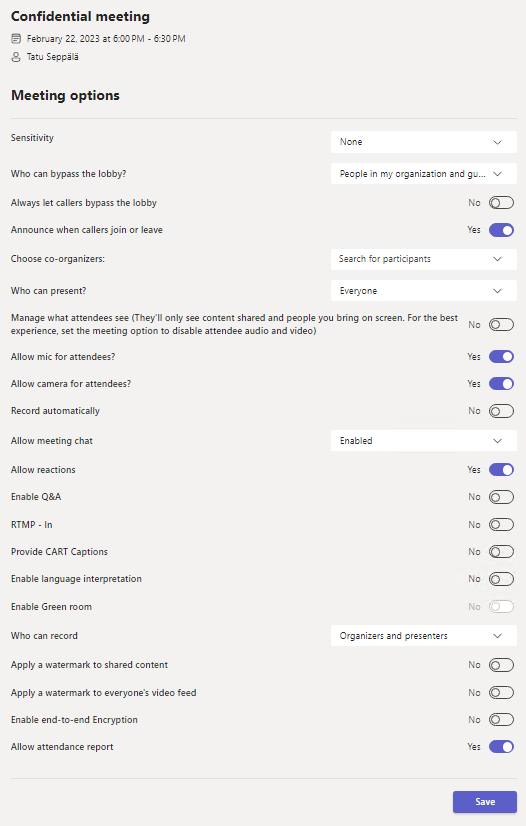
Right now, if you want to create a more secure meeting, you’ll have to..
- ..get familiar with every control on that list.
- ..understand and remember how to use them to avoid unwanted outcomes.
- ..expect everyone else that books meetings in your organization to also read, understand and consistently remember use them.
It is absolutely unlikely that this will happen in most organizations. There’s simply too much choice, it’s too well hidden away and the effects of every setting aren’t even clear to people. Plus many have never even heard of the meeting options screen to begin with.
But we can and even like to make choices. They just have to be simple and intuitive ones, such as..
- Fish, chicken or vegetarian?
- Tea, coffee or just water?
- Adventure holiday or relaxing beach vacation?
- Public, general or confidential information?
This is the real benefit of sensitivity labels regardless of where they are used. They help condense a multi-faceted and deep series of decisions across various interfaces into a single, easily accessible decision point that most people are equipped to make.
Making simpler choices
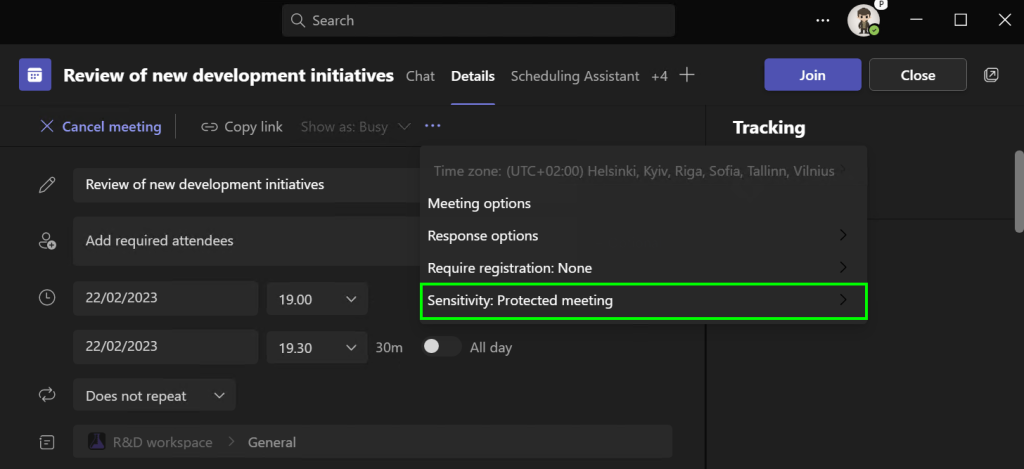
In meetings, sensitivity labels can be applied without ever diving into the web-based meeting options screen. For easy access, sensitivity labels are surfaced right in the meeting creation screen in Teams.
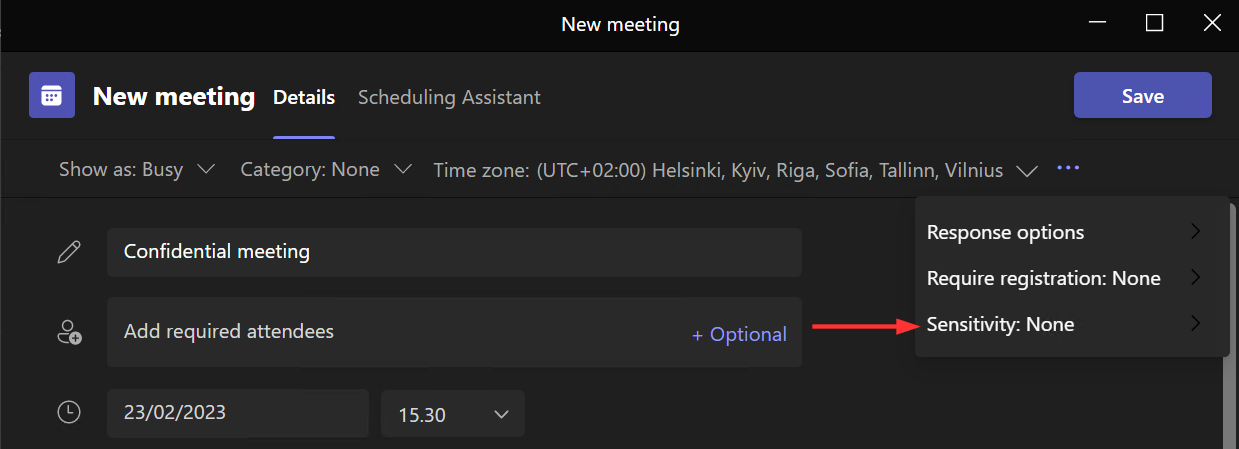
This capability has still been a bit broken for me during the preview and I’ve had to set the label in meeting options, but that’s just fine and dandy, because it’s important we have look at what exactly applying a sensitivity label does to the meeting.
When selecting the desired label, we can show a tooltip description of what the label’s effects are – or something else, depending on how we configure the label.
Side note: The ability to customize this tooltip specifically for this user experience is currently the only reason I would create separate sensitivity labels just for Teams meetings – and I really hope Microsoft brings the ability to customize label descriptions for each context separately without having to resort to this.
Zooming out, we can see the full effects of our choice on the meeting’s settings. I’ll try to highlight the critical ones for you here.
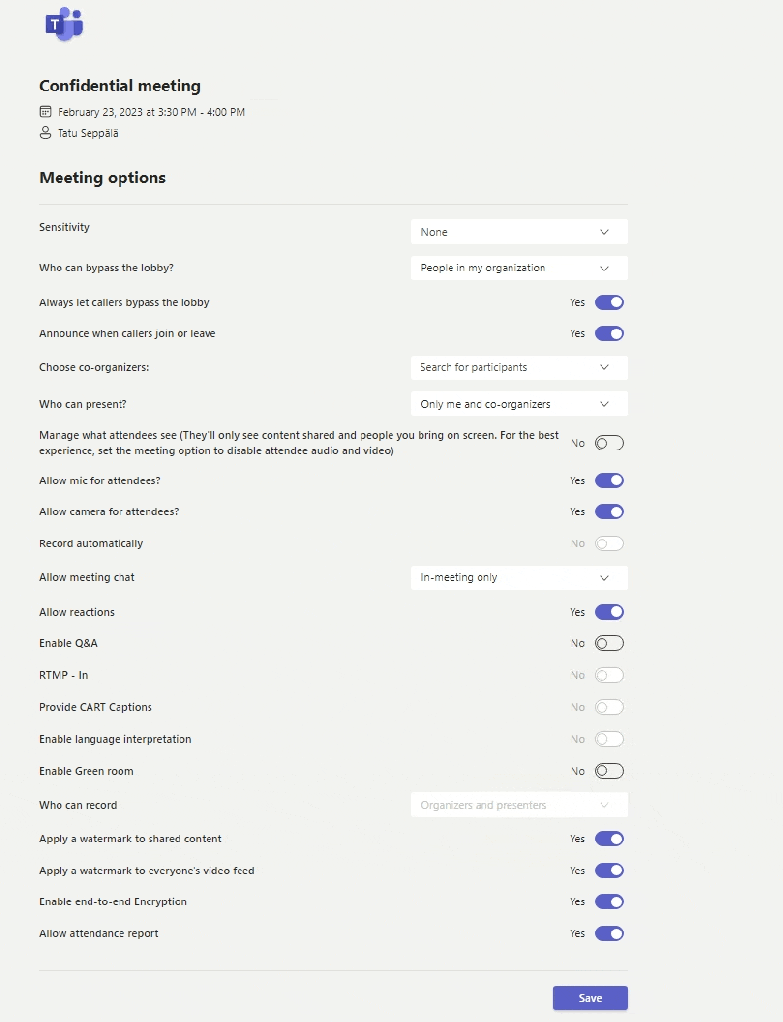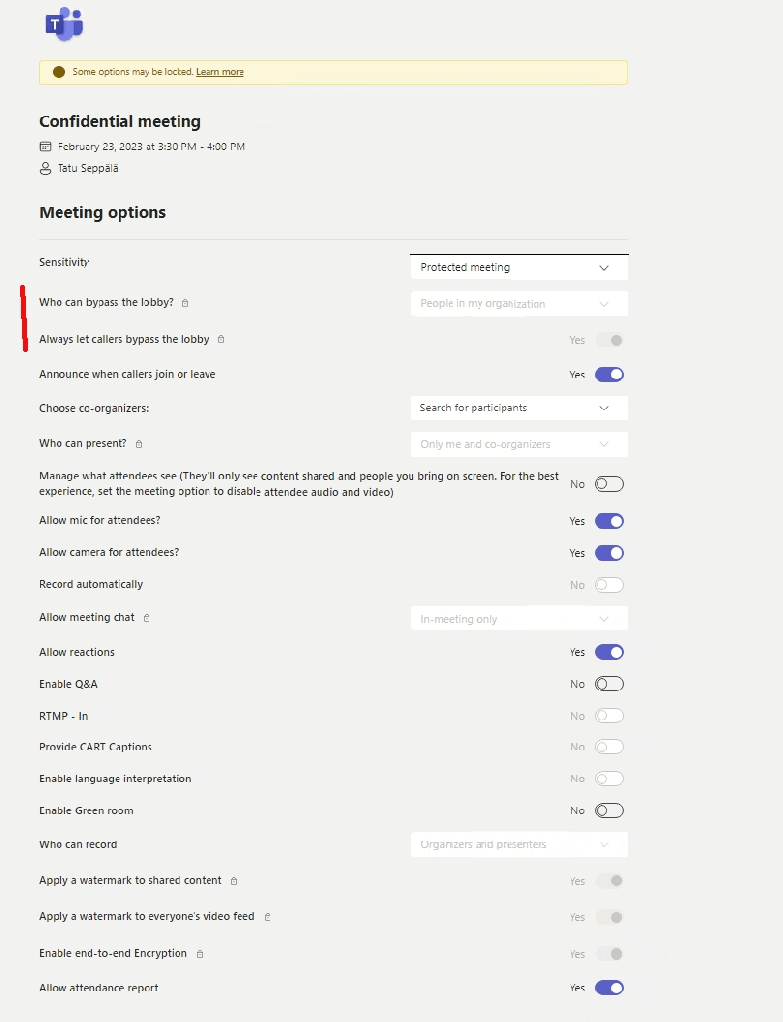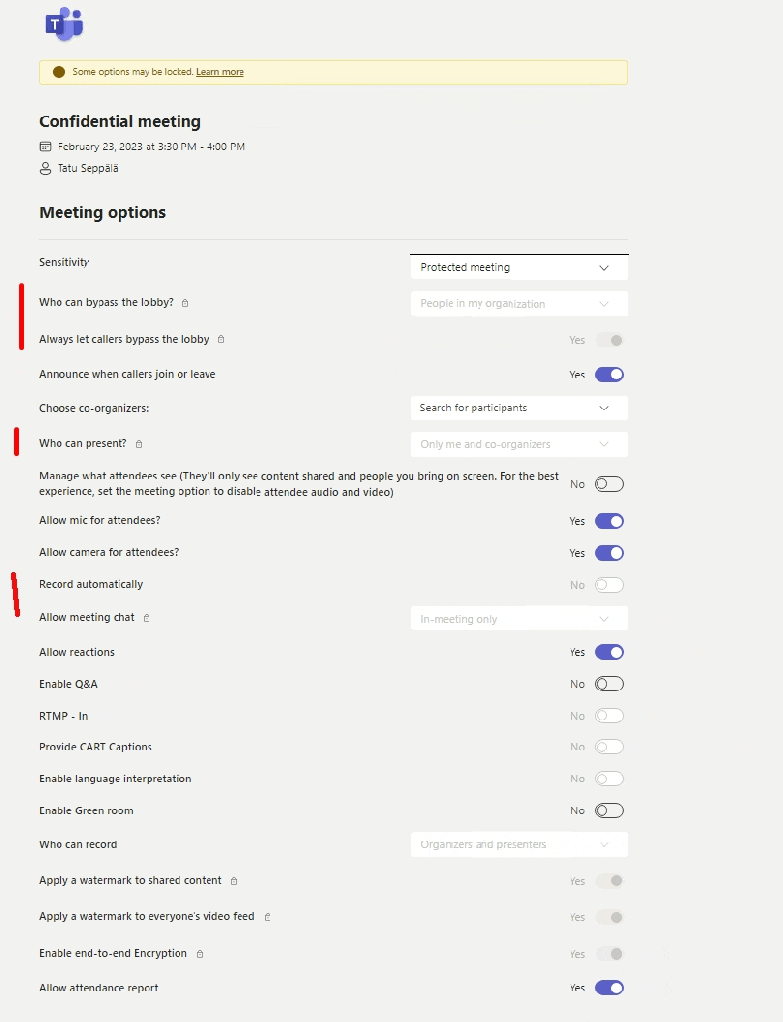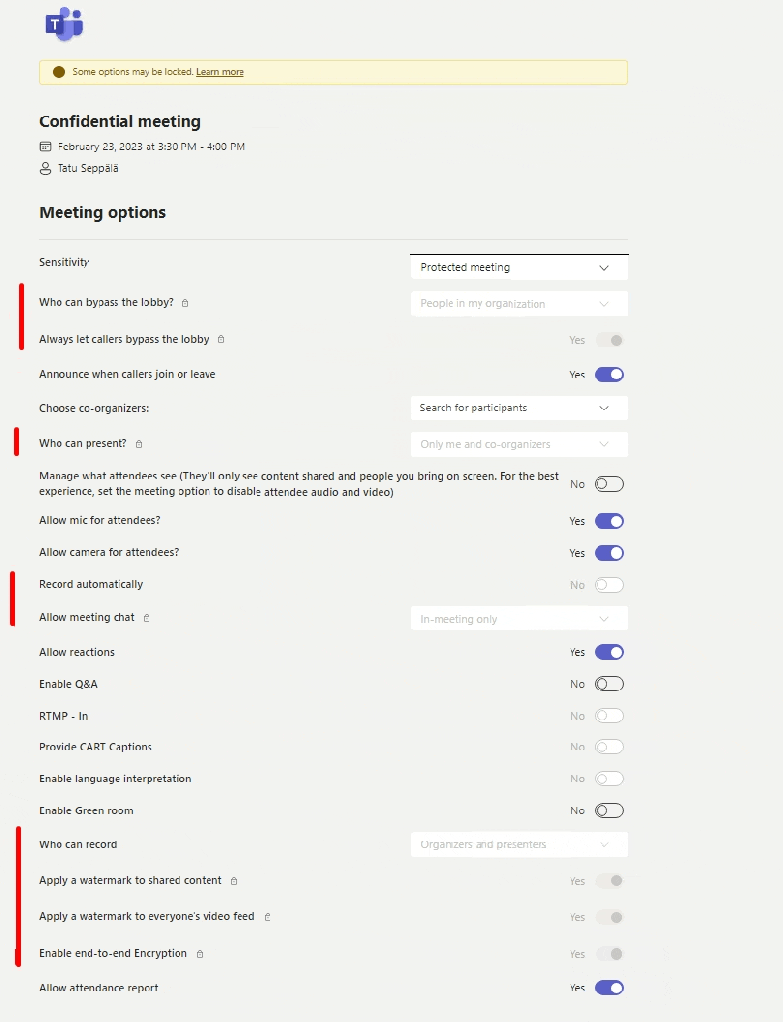
As the administrator, I took a good look at the available options and pre-configured the Protected meeting label to enforce certain settings when the label is applied. This includes things like:
- End-to-end encryption for all meeting participants
- Automatic and personalized watermarks to the shared video feed for all participants
- Lobby control – only allowing internals to join all the way without approval
- Presenter rights only for designated organizers
- Chat only allowed during the meeting
- etc.
I also configured some additional hardening that isn’t available through the user-facing options such as a restriction on copying content from the meeting chat, which we’ll take a closer look at shortly.
All of this has the net effect of utilizing meeting options with purpose to create a centrally-managed, repeatable and more secure meeting experience without forcing people to do tedious things like reading documentation or crawling through menus to click at a myriad of buttons and switches.
In fact, in real life that documentation will usually be neglected even if it’s readily available, and those menus will never be opened. That means sensitivity labels might be the only way to consistently help people effectively secure their meetings across the board.
On top of the controls directly related to meeting settings, when properly configured meeting labels will also apply a corresponding sensitivity label to any email sent through the meeting invitation, starting with the meeting invite. This enables applying encryption, markings and Data Loss Prevention controls to these emails, allowing protection to flow from the meeting to related communications.
Let’s hop into the meeting to check how my chosen set of security controls present themselves in the user experience.
The meeting experience
The following is a closer look at some of the key protections available to meetings through sensitivity labels.
End-to-end encryption (E2EE)
First, a caveat on clients. The web client for Teams doesn’t currently jive with end-to-end encryption (E2EE) for Teams Meetings. If you try to use Web for such meetings, you’ll get this message.
I’m happy there’s an actual native error message at least. E2EE is a tool for situations in which regulation or laws mandate it and not something to use for the “shiny factor” alone. It limits meeting capabilities due to Microsoft not being able to use certain capabilities in the cloud infrastructure because of E2EE.
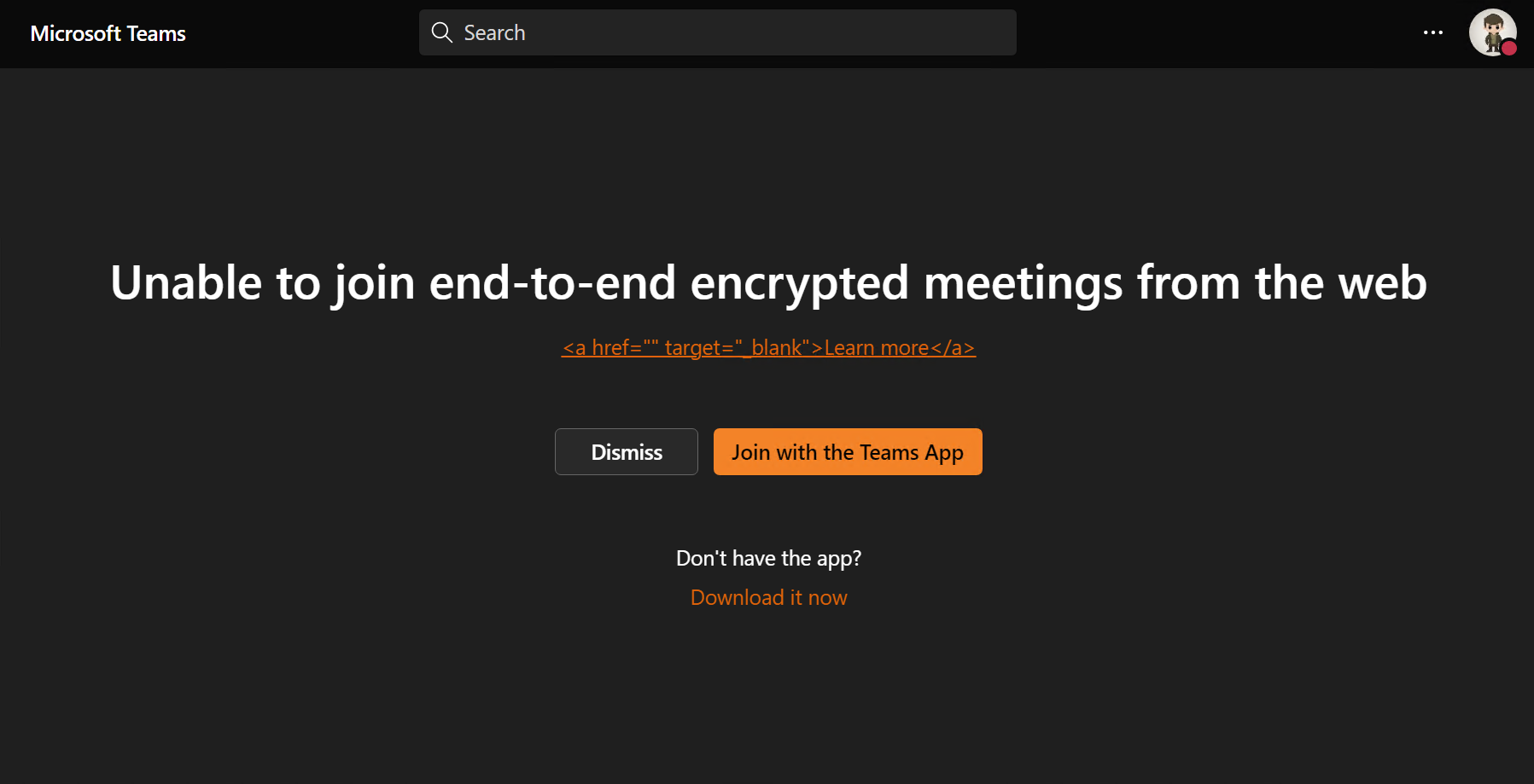
I also want to point that even without E2EE, Teams encrypts all comms with tech like SRTP and TLS.
Using E2EE for meetings disabled cloud-side features like live captions and together mode, because by design, Microsoft’s backend can’t access the video and audio feeds during transit to perform the functions necessary for those features to work.
So in any case, the Teams client it is.
On joining the meeting, you are notified of E2EE being enabled.
You can then verify that all participants are in the same meeting by checking the identifying numbers under the shield & lock icon on the top left of the meeting UI. The numbers should match for all participants, and the amount of participants in E2EE meetings is currently capped to 50.
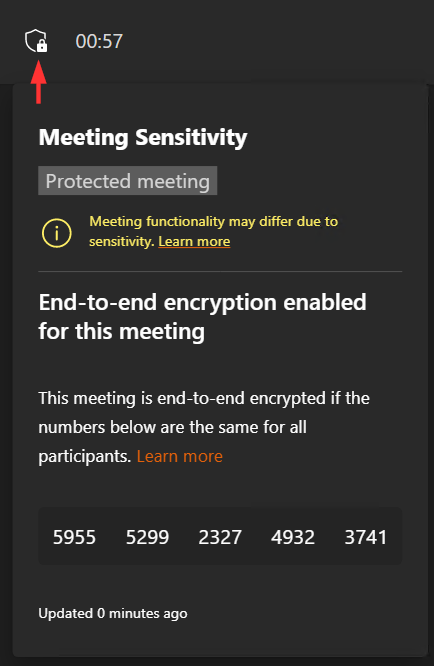
Applying E2EE through sensitivity labels is extra useful because it is a feature that can’t be turned on after a meeting has started. This means organizers have one of two options for ensuring E2EE is applied:
- Navigating to meeting options manually before the meeting begins and turning it on, which is easy to forget.
- Applying a sensitivity label to the meeting from within Teams, which is feasible, especially if it’s mandatory and/or done automatically for you.
Personalized watermarks
Once a video feed is shared in the meeting, every participant’s feed gets a personalized watermark showing their own username plastered over the shared content.
This is obviously meant to dissuade people from taking screenshots (or video recordings with software like OBS) of sensitive contents they might not be authorized to capture. By the way, this also makes personalized watermarks an effective insider risk control.
Participants are informed of the watermark with a popup, although it is hard to miss either way. The watermark can be personalized or it can show the identity of the person sharing content, as desired.
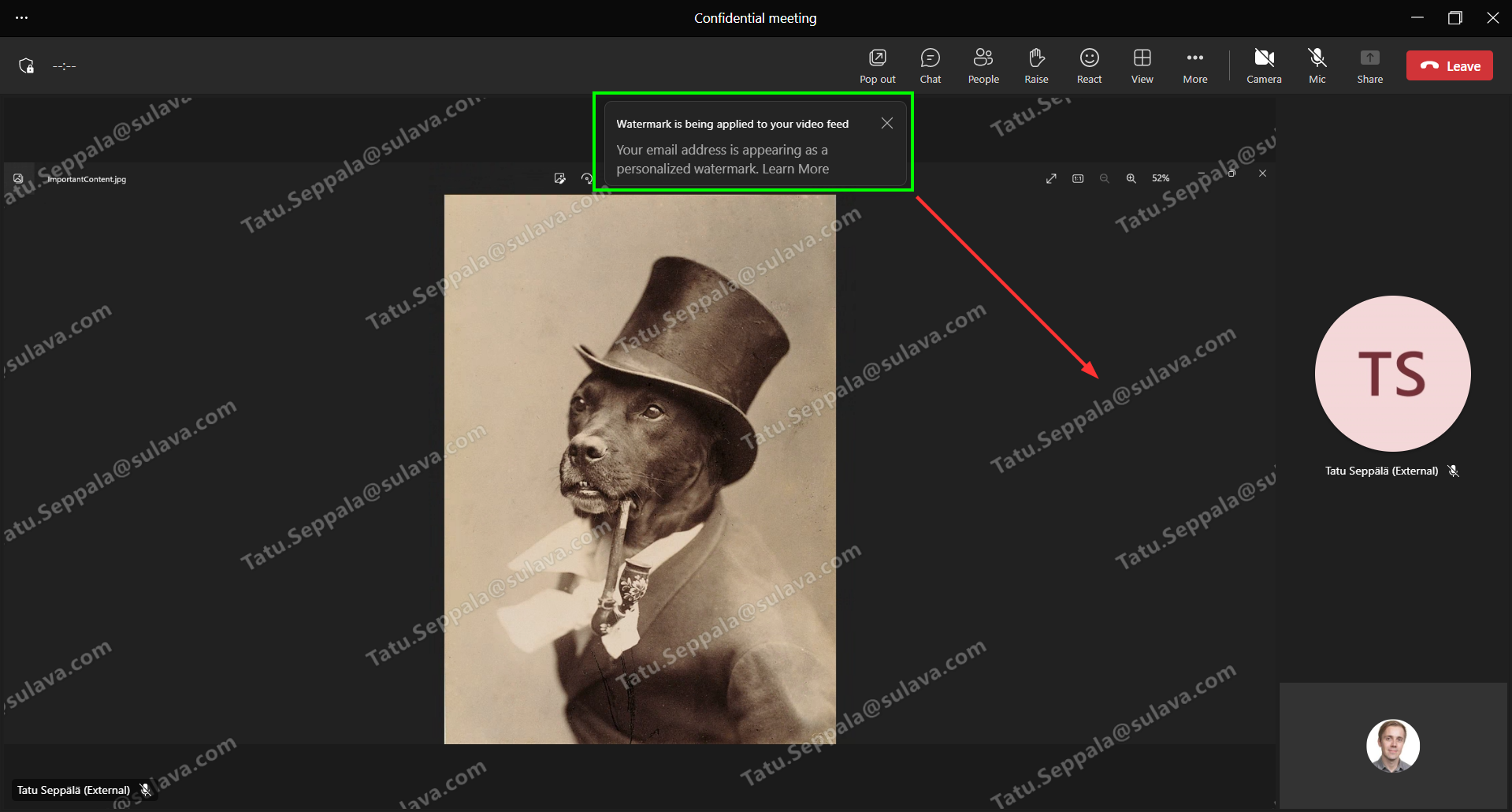
Applying a watermark also limits you from using some capabilities (notably recording). An up-to-date listing of limitations for each watermarking setting can be found here.
Chat restrictions
Chat is a key channel in many meetings that can hold a lot of confidential snippets of information for extended periods of time.
However, it is not covered by E2EE, but by Microsoft’s regular data encryption in Teams. I reckon this enables eDiscovery to work for compliance purposes, among other things.
Because of the settings imposed on the meeting by the sensitivity label, chat is only available for each participant when the meeting is ongoing. When the meeting ends, chat can no longer be posted in.
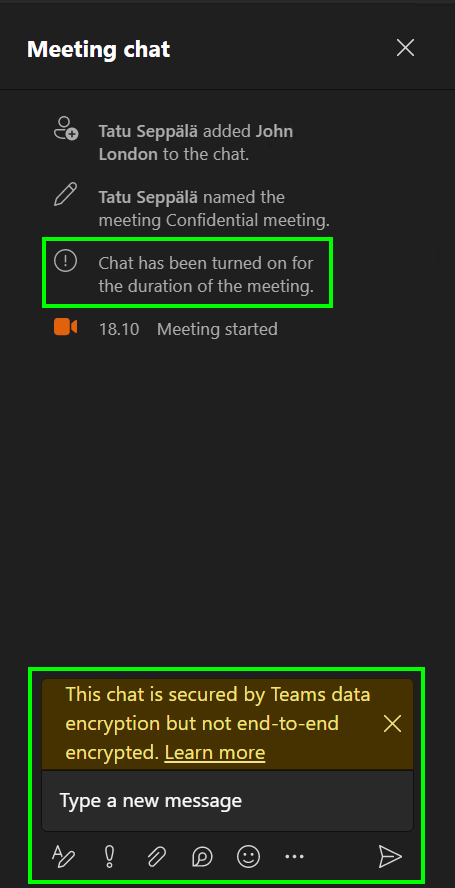
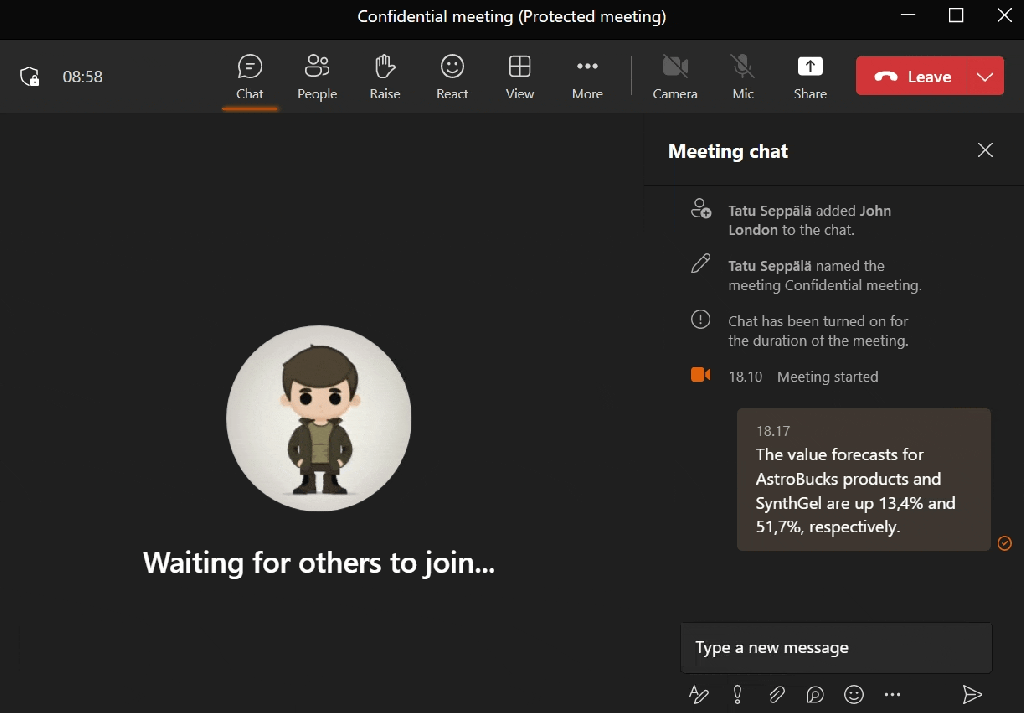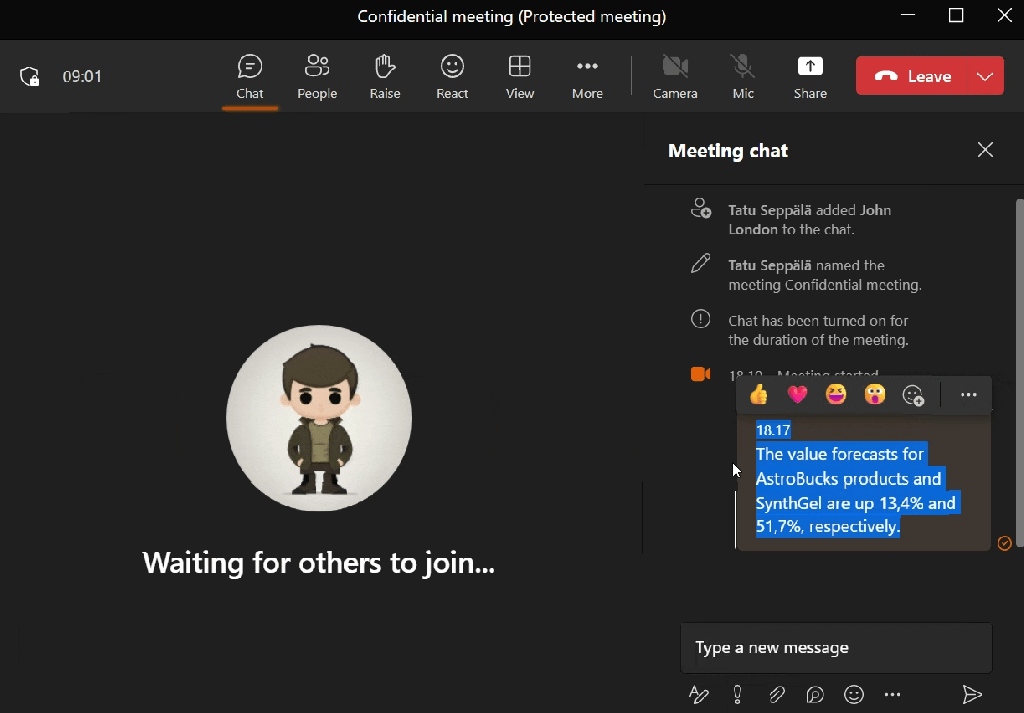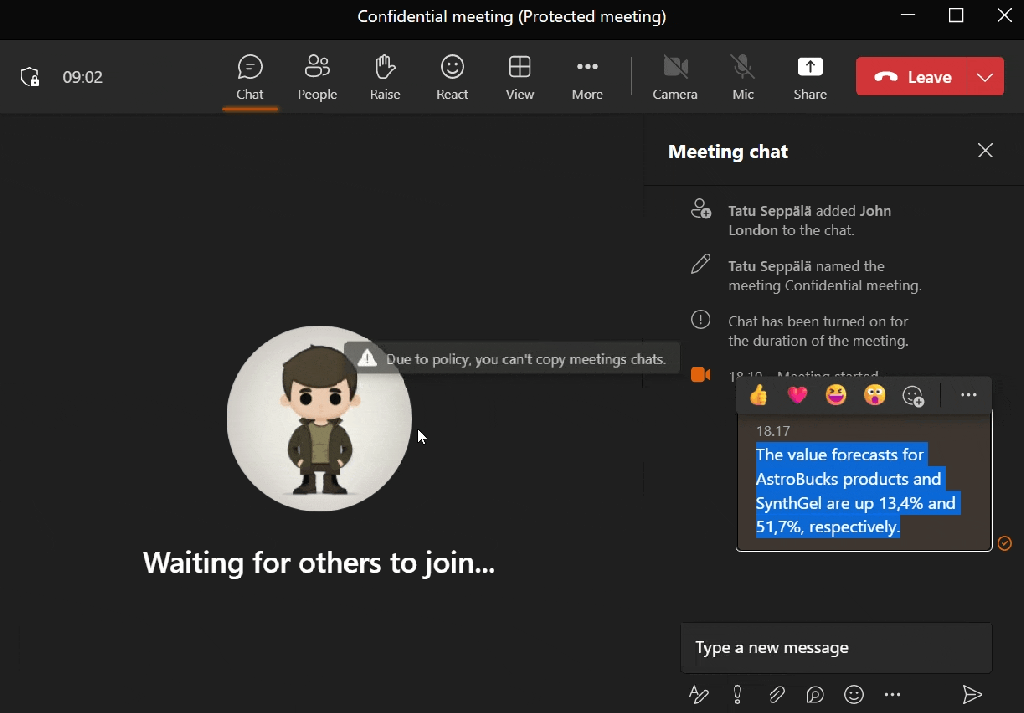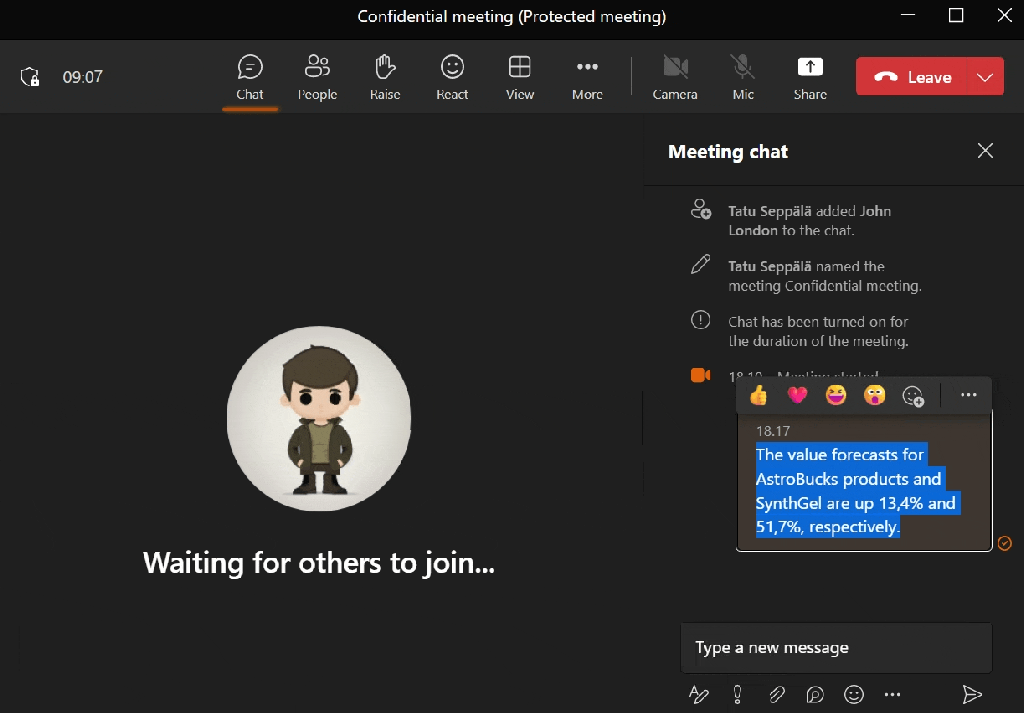
If content posted in the meeting chat should stay in the meeting chat, we can signal this to attendees by limiting their ability to copy content from it.
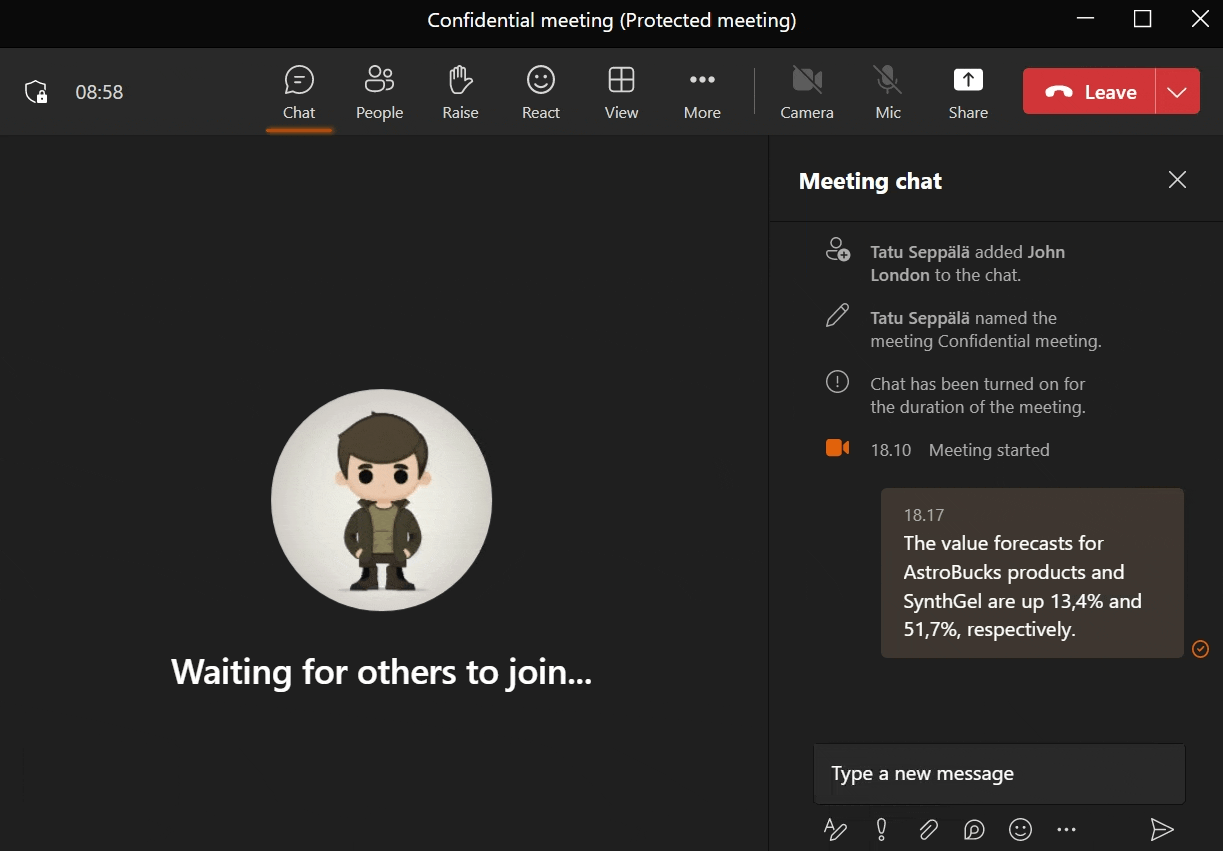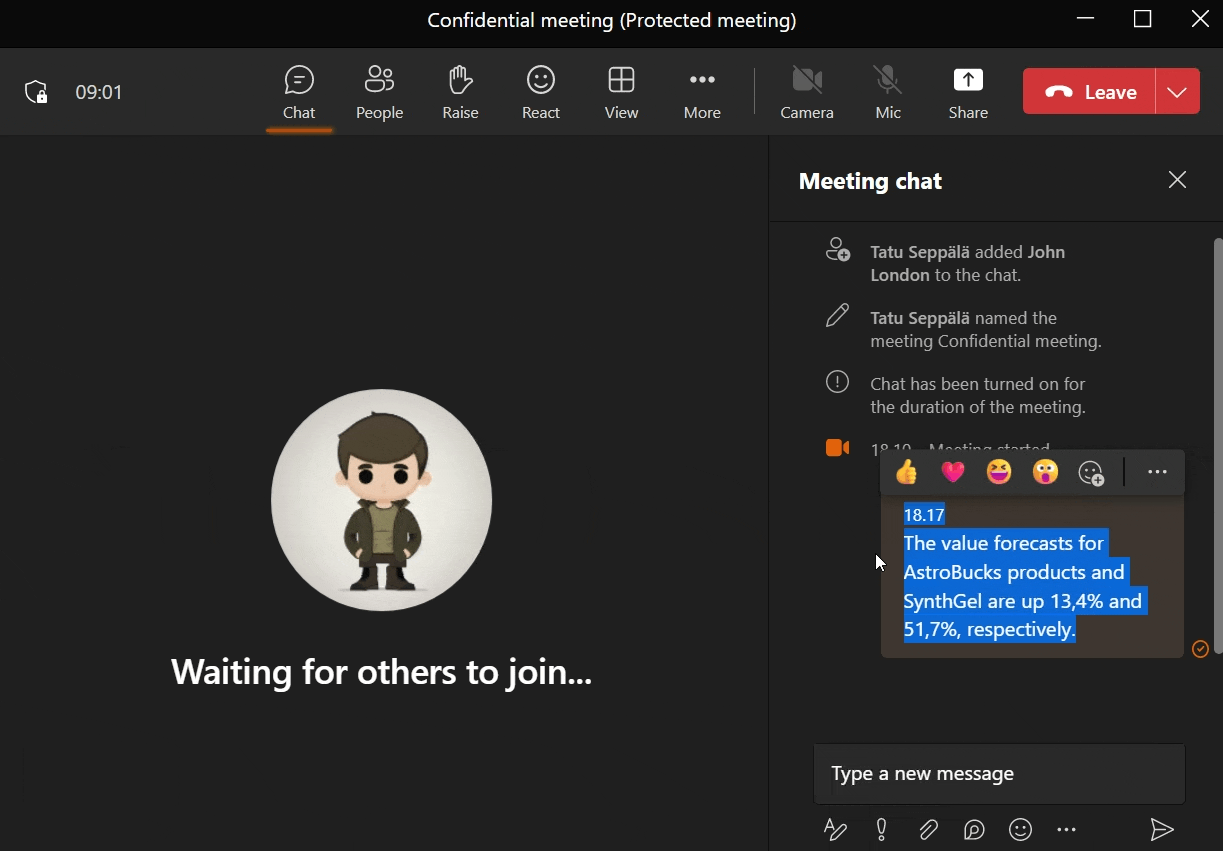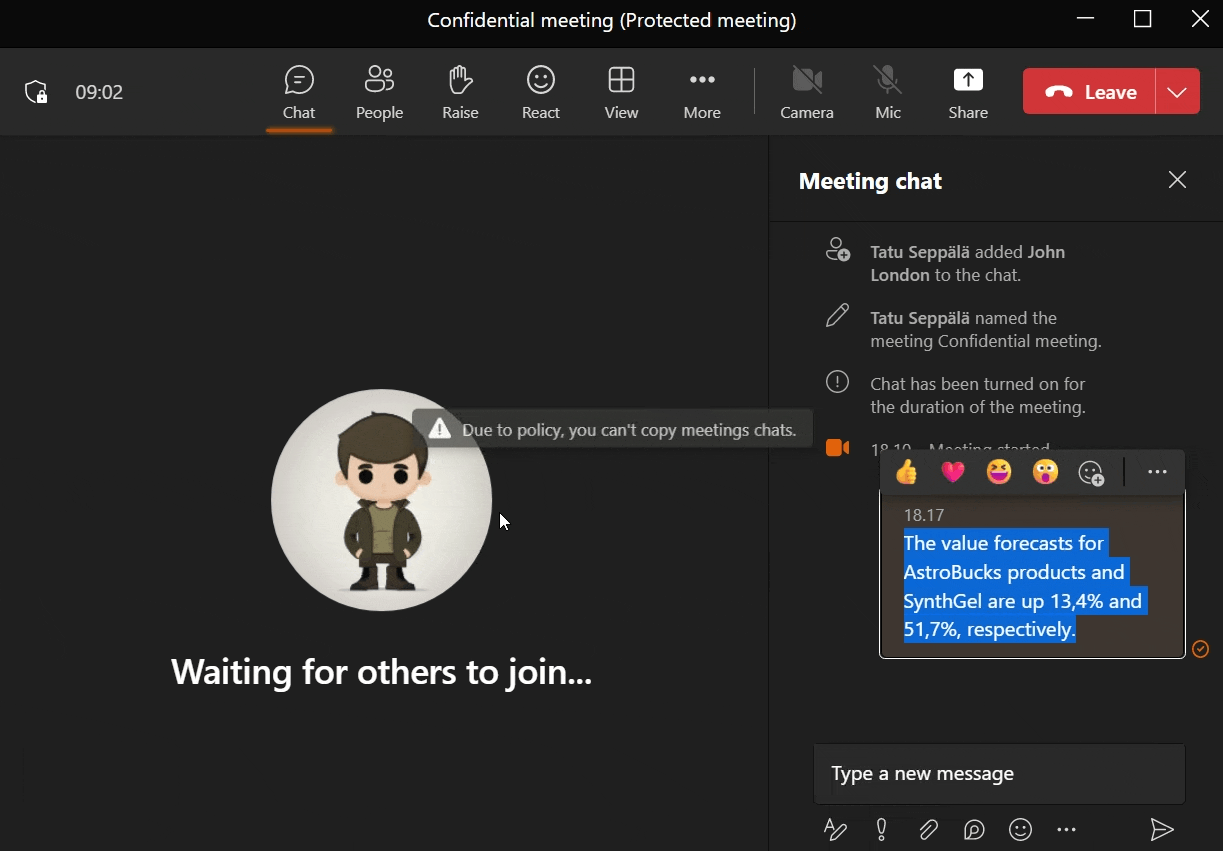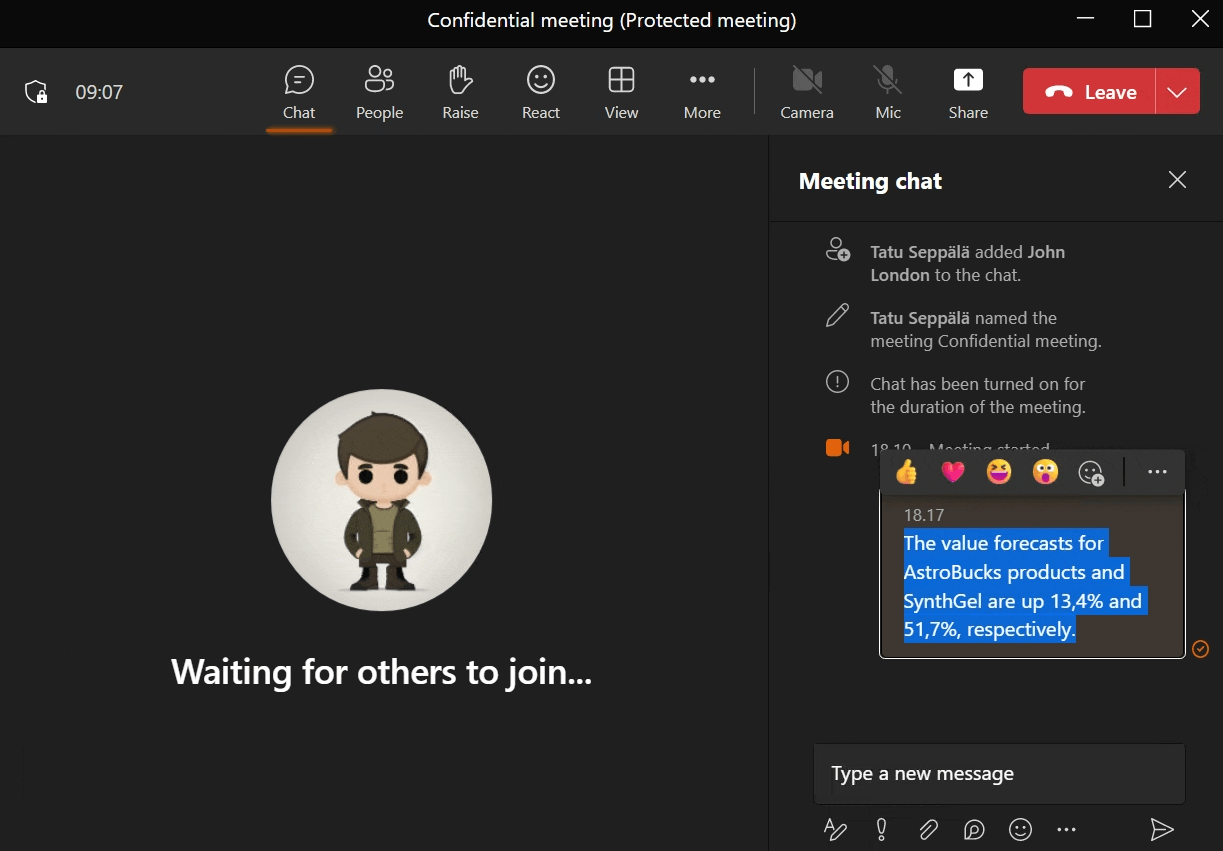
While this won’t stop anyone from simply writing down information nor from taking screenshots of the UI, it provides clear guidance of what is acceptable and what is not.
Encrypted meeting emails
Since the I prepared the communication on the admin side properly, email sent by the meeting event (like the invitation and updates to it) will be marked and encrypted.
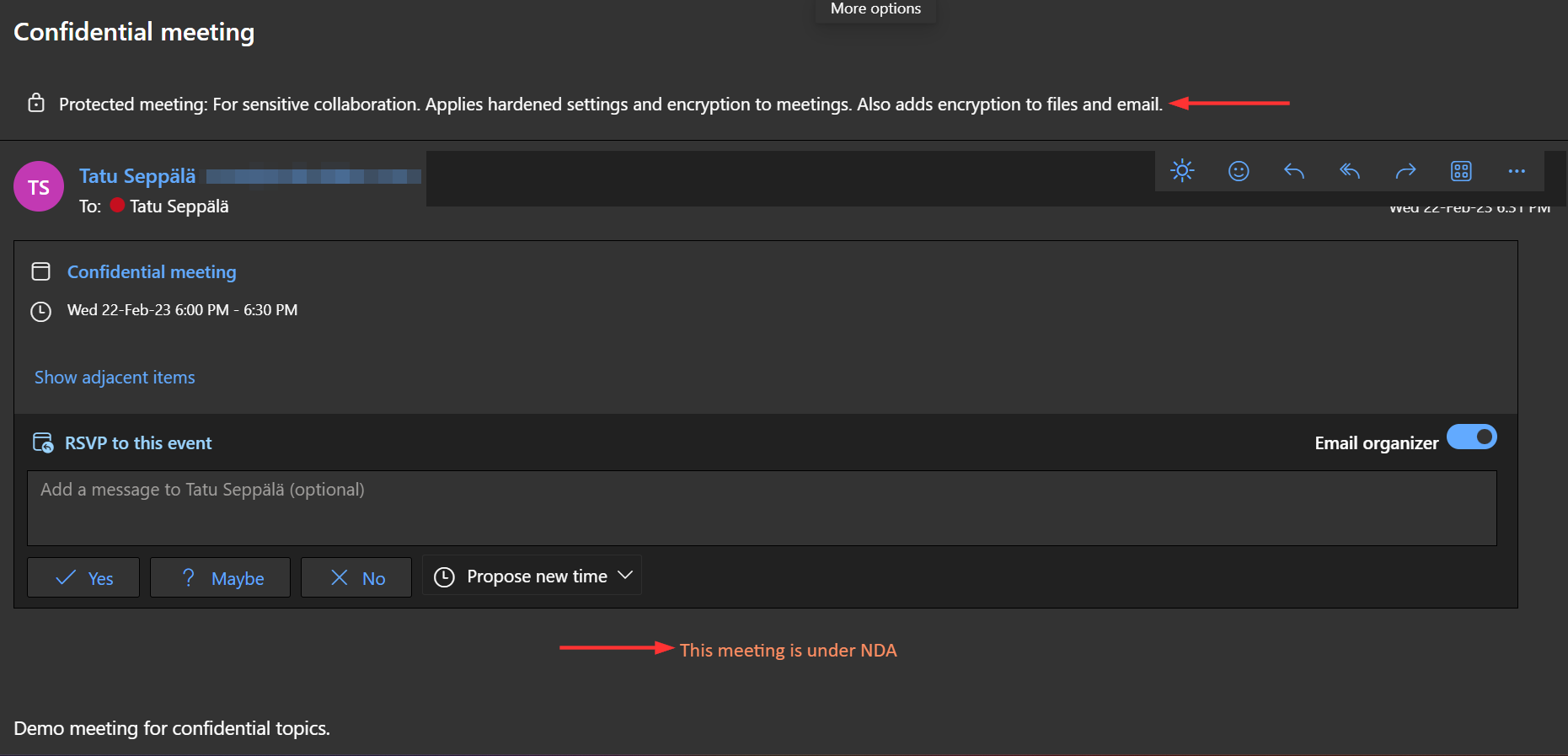
Email encryption on its own can bring in capabilities like restricting forwarding of the meeting invitation and can also prevent the contents of the invite from being shown in Teams screen sharing.
Markings (like the red text in the image above) give a tangible reminder of the sensitivity of the meeting.
Through Data Loss Prevention rules tied to the meeting’s sensitivity label, we can then further extend auditing, controls and restrictions to scenarios like internal individuals forward a meeting invitation to external recipients.
Suddenly Teams meetings aren’t a black hole anymore when it comes to information protection.
But if this was all there was to it, I still wouldn’t be happy. There’s one key aspect we haven’t discussed yet that – the one missing puzzle piece to bring the story home.
Sensitivity-aware workspaces
I’m a firm believer in context-based automatic sensitivity determination being a key factor in a mature information protection strategy. When we build our strategy around sensitivity-aware workspaces, we can get let our information protection capabilities out of people’s way as much as possible without compromising with protection.
With sensitivity-aware workspaces, I specifically mean sensitivity labeled Teams teams / Microsoft 365 groups and SharePoint sites.
When we do work, collaborate and handle information in a sensitivity-aware workspace, the controls for our collaboration experiences like meetings and for the information we produce should just flow from the context we’re working in.
Confidential team -> Confidential meeting -> Confidential files by default – and so forth.
Let’s run through a quick example.
Sensitivity inheritance
When sensitivity labels for Teams teams are enabled, the creator and initial owner of the team is asked to determine the sensitivity of the workspace as part of the creation process.
The choice can be made easier by providing understandable descriptions for each classification.
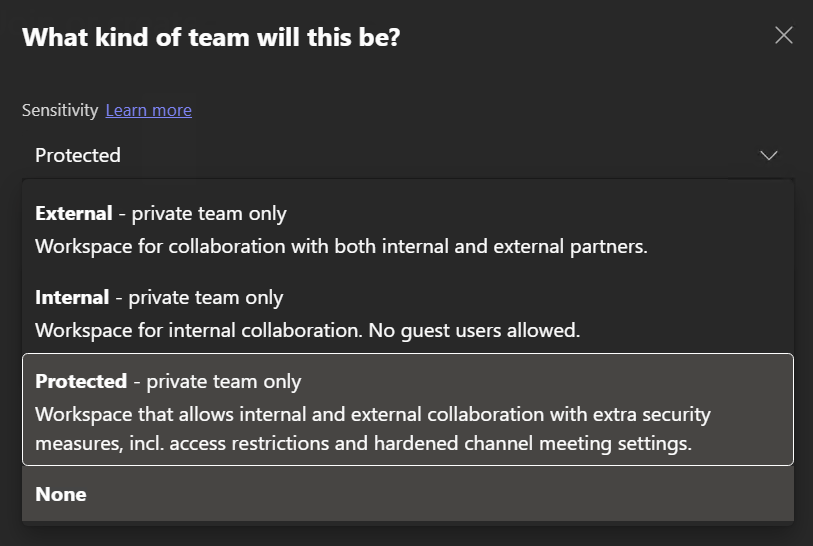
When the team is classified as Protected, admins can ensure all meetings are enforced to follow a corresponding sensitivity label and associated settings.
Let’s say I run a team for a Research & Development team and we’ve just created a Protected team as the context for our daily work. We need to create a sensitive review of recent development activities as a channel meeting, but don’t really know anything about meeting options.
As one of the team owners, I’ve taken responsibility of booking the meeting. I create the channel meeting..
..and I just give it a name, then send out the invitation.
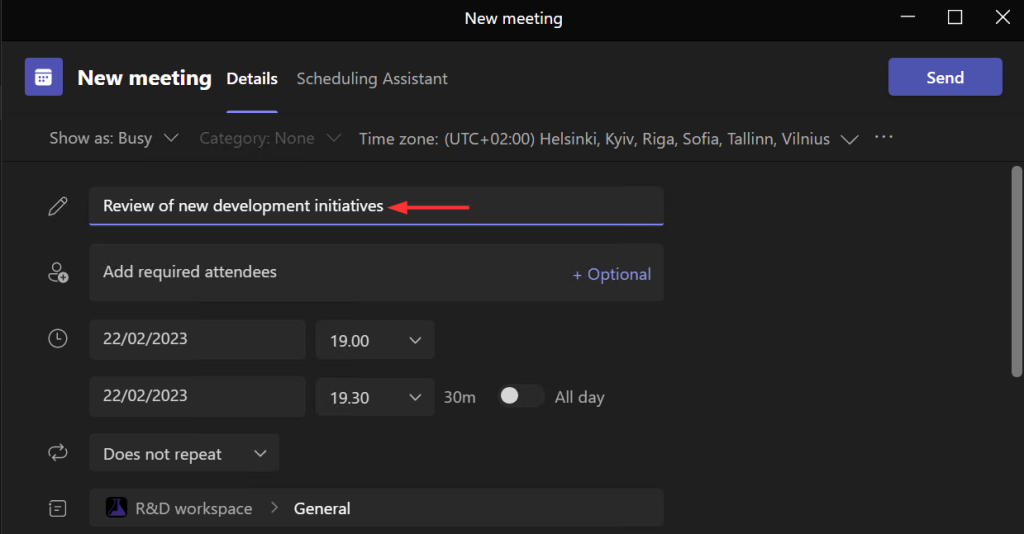
Normally, the meeting wouldn’t get any protections – but since my organization has attached the ‘Protected Meeting’ sensitivity label to the ‘Protected’ team sensitivity label, channel meeting gets labeled automatically and I don’t even need to understand all of the exact options that are set on the background. “It just works!”
We can then expand this by also configuring the Team’s SharePoint site’s document library to automatically set a specific default sensitivity label to all unlabeled documents uploaded to the team, all of which then get the benefit of encryption, markings, DLP and auditing – and in turn start to feed new signals to solutions like Insider Risk Management.
All of this is pretty neat, but needs to be implemented very thoughtfully to support real organizational requirements without imposing any unnecessary restrictions on the user experience.
In fact, a positive user experience must be protected at all costs. If their experience with a tool or platform sucks, people don’t want to use it – and if we have Teams, we want people to feel comfortable using it to its fullest.
I’ve saved the elephant in the room for last, so here we go..
Licensing
Long story short, sensitivity labels for Teams meeting requires Teams Premium add-on licensing.
But wait! Not necessarily for everyone in your organization.
The exact licensing approach is subject to change and should be checked from Microsoft sources like this article in Learn, but the general idea is that add-on licenses are only required when a user benefits from one or more of the services included in the license.
This means you could only target Teams Premium for business functions that really need the additional protections and various other collaboration-enhancing and AI-driven features the most, like C-levels, HR, Comms, Legal, Risk management, R&D.. but not necessarily every firstline worker, for example.
The story continues
I doubt this will be the last batch of security controls we see for Teams Meetings and I’m happy they are being addressed.
I’ve felt that online meetings have been a bit of a Wild West for a long time now because you usually both get to bring in unauthenticated outsiders while simultaneously sharing all kinds of content without exact auditing or controls to curtail misuse or accidental exposure of sensitive information.
Hopefully we keep walking this path of bringing meaningful controls that can also be built in a way that doesn’t involve people clicking through a million menus and buttons to unlock their value.
See you next time! ✌️